All along, everyone thinks that the CAN bus is almost impossible to protect. But Trillium's SecureCAN clearly broke this "superstition."
This article refers to the address: http://
Technology products in the field of automotive safety are becoming hot. A large number of startups are pouring in, and while concentrating on technology development, they are looking forward to becoming the next target for large company acquisitions. Last summer, white hat hacker Charlie Miller and old partner Chris Varasek invaded a Jeep Cherokee. Almost at the same time, GM Anjixing's RemoteLink system was blasted with security holes. The hacker used the system gateway to remotely control the door to unlock and start the engine. The picture below shows the 15 most vulnerable attack surfaces exposed by Intel on the current connected car.
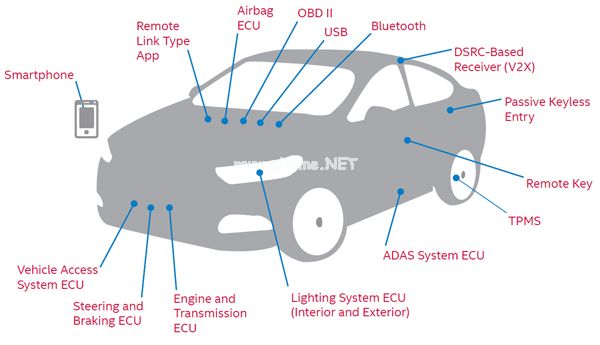
Therefore, according to the current situation, the more energy companies and suppliers invest in smart connected and self-driving cars, the more they attach more importance to safety, and the network security is becoming smarter and more automated for the automotive industry. The direction of development is playing a pivotal role.
In the article "CES Preview: In 2016, these seven "small companies" are the vane of automotive technology", this article introduced the Japanese startup Trillium and carried out its car safety protection tool "SecureCAN". Brief description. Nowadays, car networking and autonomous driving are flourishing. As a startup focused on the field of car safety, how does Trillium view the safety of smart connected cars? What is the competitiveness of its products? What kind of technological development route will be adopted in the future? Don't worry, we chatted with Trillium CEO David M. Uze, and there must be an answer below.
Oh, this is Trillium.
Trillium was founded by David Uze, former president of Freescale Japan, and is headquartered in Nagoya, Japan. Last fall, Trillium "intrusion" into the automotive safety field with "SecureCAN" technology. This car safety protection tool called "SecureCAN" can encrypt both the CAN bus and the key management, and the protection system payload is no more than 8 bytes. The key to this technology is that SecureCAN can process data in the "8-byte" range without the 128-bit encryption bits required by the AES encryption algorithm Rijndael.
Uze believes that due to the lack of a security solution for the ECU network, CAN is a native unencrypted bus in the automotive system and does not undergo any security processing. Therefore, the hacker can obtain the authority to control the steering, braking and other functions of the car through the CAN bus. For this reason, the CAN bus has also become a "land of happiness" for many hackers. In addition, the protection gap in the local interconnect network LIN, usually used to control the rearview mirror, window or skylight, is likely to become a "back door" for hackers to invade the CAN bus.
For a long time, almost the entire automotive industry has the consensus that the CAN bus cannot be protected. For two reasons, first, the ECU's computing processing capacity is insufficient; second, the bandwidth of the in-vehicle network is limited. Some LIN buses use MCUs even 16bit or 8bit, but the encryption algorithm used by AES can only process 16-byte blocks of data, which means that the LIN bus is often in a "streaking" state.
David Uze said in an interview that SecureCAN is able to encrypt CAN and LIN bus information in real time due to the use of ultra-lightweight block ciphers. It is worth mentioning that the symmetric block cipher and key management system enables SecureCAN to complete the "encryption, transmission and decryption" process within a threshold of 1 millisecond. This is crucial for the real-time encryption and decryption of the car CAN bus.
Since the launch of the SecureCAN sample last fall, Trillium has been refining this safety protection tool throughout the year. Although the original SecureCAN sample used the ARM Cortex M4 processor, Trillium had to choose the ARM Cortex M0/M01 after the chip supply problem, but lost the floating point operation but also wanted to implement the SecureCAN preset function. Trillium is really a big challenge.
According to Che Yunyu, the latest SecureCAN test version adds public key technology and uses the Diffie-Hellman key exchange algorithm to generate keys. The following picture shows the root of the trust chain of SecureCAN.
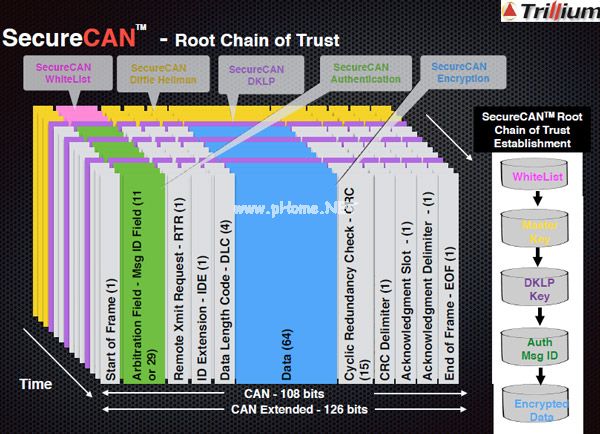
SecureCAN is just the first step
It is clear that Trillium's "SecureCAN" technology solution has solved the problem that was previously considered "impossible". However, David Uze also foresees higher requirements from OEM OEMs and Tier 1 suppliers. They hope to get a complete set of security protection technology solutions, not only in-vehicle networks, but also V2V/V2I communication, OTA upgrade system, intelligent firewall, etc. can be tightly protected.
On June 30, 2016, Trillium received a $5 million Series A financing, and naturally its product target was also "high." In addition to the CAN bus, Trillium is also working to incorporate the protection of FlexRay and LIN bus into the entire in-vehicle network protection system. In addition, Uze said Trillium used the investment to integrate existing engineering resources to ensure that all projects can operate in parallel, including the development of intrusion detection and prevention systems (IDS/IPS) and OTA software upgrade solutions. .
In line with Uze's goal for Trillium, Trillium will provide a range of automotive safety technologies based on the same platform and unified API port. SecureCAN will begin real vehicle testing this month. A Japanese car (Uze refuses to reveal the brand and model) will be equipped with Trillium's SecureCAN/Ethernet technology. In January next year, Trillium will launch the testing of SecureFlexRay/LIN technology in the car. (The FlexRay bus is typically used to transfer data related to ADAS sensors). In addition, according to Trillium's plan, the Intrusion Detection and Protection System (IDS/IPS) and OTA air upgrade technology will be tested at the end of 2017.
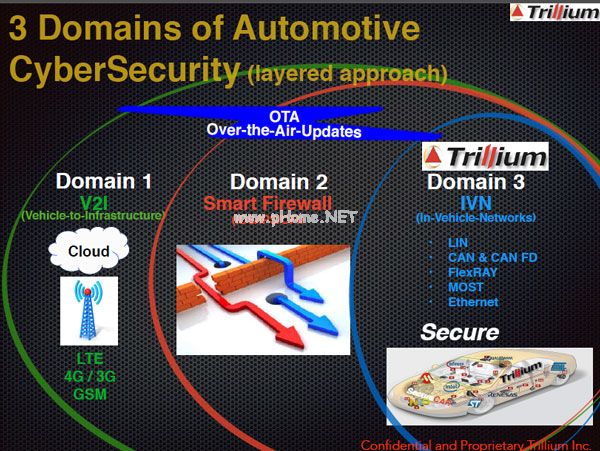
Three major areas involved in automotive network security
Multiple Attack and Defense of Car Information Security
However, Uze also said that "protecting the CAN bus is not the only good strategy for the automotive industry to deal with network security issues." He believes that for future connected cars, a variety of different security measures should be taken.
Previously, when asked about "CAN bus encryption," Timo van Roermund, security architect at NXP Automotive, said, "Key management is one of the most important parts, especially when used to protect ECUs. Information is very important." However, Roermund also pointed out that different OEMs may choose different in-vehicle network architecture management solutions, and there is no such thing as a "standard method" for key management.
The following are some of the most common network security measures taken by the host manufacturers and suppliers.
1. Use a firewall to isolate the in-vehicle electronic system from the external interface;
Molded Waterproofing Cable Assemblies
We specialize in waterproofing products overmolding. We can custom build, custom mold, and over-mold your cable designs.
We specialize in molded cable manufacturing for the widest diversity of
cable and connector types, across the whole spectrum of industries. Rich expeirence in developing and proposing solution Special for IP67, IP68 waterproofing products.
Molded waterproofing cable assemblies, waterproof wire harness, waterproofing cables overmolding
ETOP WIREHARNESS LIMITED , http://www.wireharness-assembling.com