Lei Feng network: According to author of this article is Siyuan Kean iris algorithm engineer.
Recently, Samsung Galaxy Note7 was officially released. As a new generation of Samsung, the new function of iris recognition has become one of its highlights, attracting public attention.
The role of iris recognition in addition to the well-known iris unlocking, but also added some extended application elements. For example: folder encryption, mobile payment, access to the Samsung App Store, and the opening of the Samsung Pass feature, allowing developers to integrate iris recognition technology with applications.
Iris recognition in the end is what kind of technology, why will Samsung bet on the latest flagship?
To decrypt iris recognition, you must first understand what an iris is.
The iris is the muscle that regulates the size of the pupil outside the eye and controls the amount of light that enters the eye. It is the colored part of the eye that is formed based on the amount of melatonin. Although the color and structure of the iris are linked to genes, the details are different. During the embryonic process, a tight and folded group of irises is formed. The prepubertal pupils are opened and metamorphosed to form a unique, unique iris pattern. Therefore, although the genes are the same, each person's iris structure is also different, which makes it applicable to identification. . Iris recognition technology is to confirm the identity by shooting the iris of the human eye. It is a biometric-based identity authentication technology, also known as biosafety technology. Iris recognition has become a hotly-recognized authentication technology in many fields in recent years because of its high security and convenience.
| Well, iris recognition mobile terminals is how to achieve?
First, the micro iris module is to be integrated into the mobile phone. The module is mainly composed of a CMOS image sensor, a dedicated micro-optical lens, an infrared filter, and an external structure (see Figure 1).
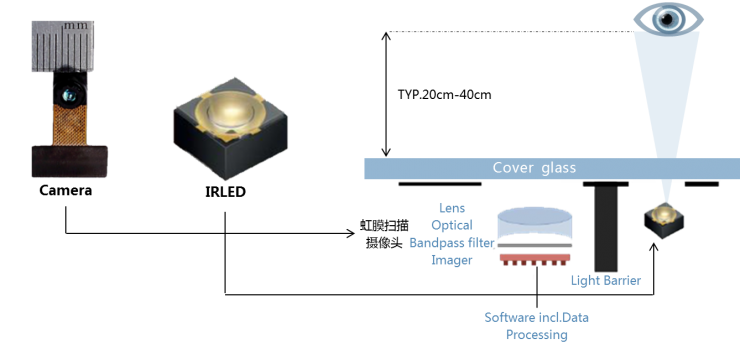
figure 1
The image sensor of the iris recognition module is improved from the currently-used color image sensor, and the photosensitivity of the infrared part is improved. A dedicated iris recognition lens is mounted, and iris images can be acquired in a range of 25 cm to 60 cm.
The core of iris recognition is iris recognition algorithm technology.
In general, iris recognition algorithms typically include iris image quality assessment, iris region location (including coarse and fine orientation), iris preprocessing, iris feature extraction, iris template generation, and iris template matching.

Figure II
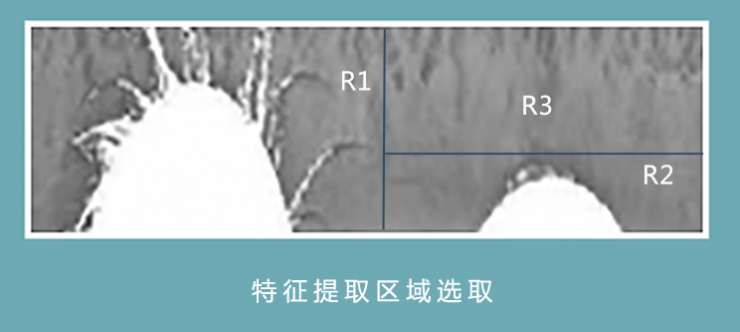
Figure 3
After acquiring the image from the camera of the mobile phone, the initial quality assessment of the collected image is performed first , and the basic parameters such as the definition, brightness, motion blur, and focusing degree of the image are evaluated . If the image does not meet the quality requirements, the discard will continue to acquire the next image. image.
When the image satisfies the requirement, it enters the iris region to be positioned. The approximate area of ​​the iris is coarsely positioned first, and then fine positioning is performed to obtain the center coordinates and radius of the pupil and the iris, respectively.
After obtaining the iris region, the interference factors such as eyelids, eyelashes, spots, and the like are removed by a preprocessing algorithm, and the remaining usable iris regions are taken out for normalization .
Then feature points were extracted to normalize iris image analysis. As shown in FIG. 3, the R1 region is severely disturbed by the upper eyelids and eyelashes, the R2 region is disturbed by the lower eyelid, and the iris texture is mainly concentrated in the region close to the pupil, so the right upper R3 region of the normalized image is selected as the feature extraction region. The size of the R3 region is generally not less than 1/6 of the normalized image size, which is 40×200. The feature region is extracted and then screened and plotted as a phasor using a two-dimensional Gabor wave. The phasor information includes direction and spatial frequency (image content) and image position.
Using these vector information to draw the "Iris code", the final use of iris code for matching authentication .


When the user activates the function, the mobile phone lights the near-infrared light source, points the glasses at the iris camera, and the camera performs imaging. The mobile phone collects the images of the camera and outputs the images to the algorithm processing module to perform iris location, extract the feature points, and generate iris creatures. The feature template, the first generated iris feature template will be stored on the mobile phone and used as a signature library for identity verification.
The subsequent real-time acquisition of iris features is matched with the stored template. After the matching is completed, operations such as unlocking the mobile phone, unlocking the APP, and payment of the iris can be completed . The intensity of the light emitted by the near-infrared light source mounted on the mobile phone to the eyes is only 1/10 of that specified in the IEC 62471 biosafety testing standard, which is far below the safety threshold and does not cause eye damage.
Iris phone is currently on the technical level, whether it is camera hardware, IR LED lighting or iris algorithm, have matured to meet the application requirements of product-level, the market has also emerged several mobile phones with iris recognition. After the popularity of mobile phones with iris recognition function, applications based on iris recognition will no longer be limited to basic applications such as unlocking and APP protection, and will further expand to rights control, network mobile payment, file data encryption, and identity authentication authentication. .
Currently, Alipay's Security Architecture Solution (IFAA2.0) has already supported iris recognition and promoted it as a highlight in the industry standard. In the near future, we only need to take a look and we can complete the identity authentication process. On the contrary, there is no need to worry about the password being forgotten and fingerprints being stolen.
Lei Feng Network (Search "Lei Feng Network" public concern) Note: This article is the exclusive release of the author Lei Feng network, reproduced please contact us to authorize, and retain the source and the author, not to delete the content.
Propane Regulator,Co2 Regulator,Oxygen Regulator,Propane Gas Regulator
Changshu Herun Import & Export Co.,Ltd , https://www.herunchina.com