As more and more embedded devices access the network and become part of the Internet of Things, cyber hackers are beginning to take advantage of these connections to achieve their own ulterior motives. Therefore, embedded devices must improve security to prevent hackers from copying IP, stealing data, or invading the system. However, for embedded engineers, security is another extremely complex topic. When designing systems for embedded microcontrollers, It is difficult to grasp what kind of protection is needed.
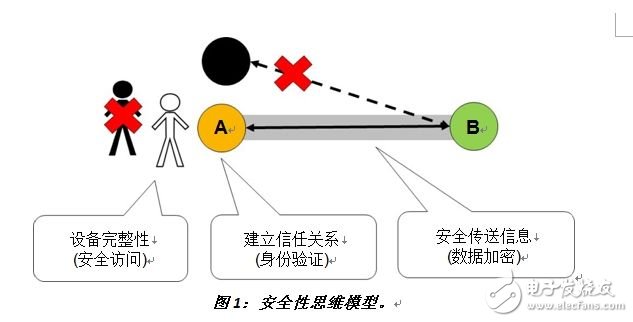
Figure 1: Security thinking model.
In order to simplify the discussion of security, we discuss it in three aspects. In Figure 1, embedded device A needs to communicate with remote device B. At this point, there are three security factors to consider: (1) device integrity – secure access to device A; (2) establishing a trust relationship with remote device B through authentication; (3) securing through data encryption after establishing a trust relationship The information transfer between the two devices is secure.
* Device integrity refers to how to prevent unauthorized access to code (or IP) and data on embedded devices (such as remote software attacks, access through established user interfaces, or physical/detection attacks on system hardware) . There are several ways to protect against these attacks, but the cost and complexity of each method varies.
* Establishing a trust relationship between devices means that one or two devices authenticate each other to ensure that data is not sent to or received from imposter devices. A common method of suggesting trust relationships is asymmetric key encryption. This method uses a pair of keys (a private key and a public key) to establish a trust relationship. The private key is used for encryption and the public key is used for decryption. Common algorithms for asymmetric key encryption are RSA and ECC.
* After establishing a trust relationship, if data is transmitted from device A to device B, the symmetric encryption algorithm will protect it. Symmetric encryption uses the same key for encryption and decryption. (This method is faster than asymmetric encryption, which is why not all communications use asymmetric encryption). The current encryption standard for this algorithm is AES (Advanced Encryption Standard). This is a symmetric key block encryption standard that encrypts 128, 192 or 256-bit data blocks using keys of the same length.
Although any encryption algorithm may be cracked under long-term attacks, even if a modern supercomputer is used for brute force attacks (meaning each key combination: 2128 or 3.4 x 103), crack AES-128 key block encryption. It may take a million years, and the AES-256 encryption algorithm has a combination of 2256 or 1.1 x 1077. Thus, both AES-128 or AES-256 are suitable for preventing brute force attacks. But in general, AES-128 is better because it is 40% more efficient than AES-256. In this way, the possibility of brute force to crack AES is almost negligible. Therefore, hackers will focus on extracting AES keys. If the AES key is not securely protected, it is useless no matter how secure the algorithm is. It's like protecting your home with a six-inch-thick steel door, leaving the key under the doormat.
Security is not a necessary rigid requirement. The degree of security required in an embedded design depends on the equipment you are connected to, the content you need to protect, and the damage caused by breaking through the security. The different levels of security available in the embedded design are listed in Figure 2.
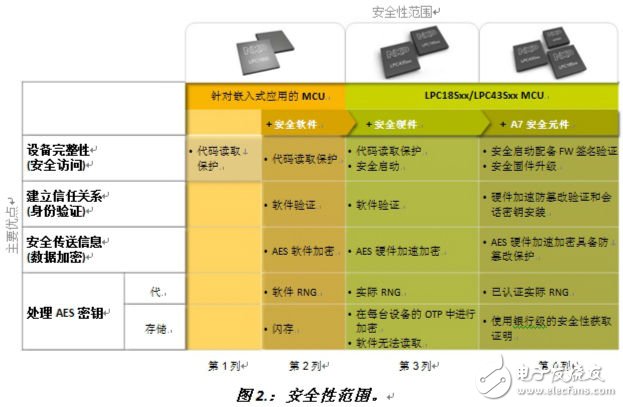
Figure 2. Security range.
The first column represents a typical embedded application. If the embedded device does not need to access the Internet, not part of the network, there is no need to use encryption algorithms, trust relationships or key storage. However, there is still a need to pay attention to equipment integrity, especially in applications where intellectual property (IP) protection is important. Preventing competitors from reading the contents of the program in the internal Flash can protect the intellectual property of the company's products from potential plagiarists. In order to achieve such protection, it is necessary to find a microcontroller with built-in code read protection.
If you need an IoT connection, you need to consider additional security features for code and data protection. Implementing software security algorithms in a general-purpose microcontroller meets all the requirements needed to securely transfer information. Software-implemented RSA or ECC can be used to establish trust relationships, while software-implemented AES can be used to securely transfer information. Keys are stored in Flash or RAM and are usually protected using software technology. However, compared to the hardware-accelerated AES implementation, the software-implemented AES algorithm is still slightly less secure.
Figure 2 also lists the advantages of replacing a general-purpose microcontroller running a software algorithm with a microcontroller equipped with hardware security features such as hardware-accelerated AES encryption, true random number generators, and improved AES key storage.
* The core advantage of the hardware-accelerated AES module is that it runs eight times faster than the software-implemented AES implementation. At the same time, hardware AES is more power efficient (requires less MCU calculations, so it is more power efficient), and takes up less code space. If you can take advantage of the hardware-accelerated AES built into the microcontroller, you can run the same soft AES encryption algorithm more efficiently.
* True "Random Number Generator (RNG)" is a physically improved version of a software implementation for creating a true random key. True RNG uses physical phenomena (such as noise) to create random numbers, while software implementations must rely on algorithms to create random numbers. True RNG is more unpredictable than software implementation. Therefore, its security is higher.
* Additional security features in some microcontrollers store the AES key in a location in memory that can only be read by the hardware IP block. In this way, the key cannot be extracted by the software.
Microcontrollers with additional security features and software encryption algorithms provide an excellent solution when hackers cannot physically access embedded devices. An example is a thermostat in a home, and you may be concerned that someone will remotely access it to hack into your internal network. However, you may not be worried about someone breaking into your house and detecting the microcontroller in the thermostat to extract the AES key. If someone breaks into your home, the problem you face is much greater than the loss of the AES key.
On the other hand, if you install smart meters outside the house, you may be more attracted to the hackers who want to physically attack and steal keys. For power companies, electricity revenue is an important asset that they need to protect. As a result, they may spend more on tamper-proof security features.
Combining a microcontroller with a secure element provides bank-level security for your embedded system (Figure 2). The Secure Element is a tamper-resistant IC that provides a secure storage location for keys and certificates; it is also equipped with hardware-accelerated RSA and ECC for faster authentication. While hardware-accelerated AES encryption is still controlled by faster microcontrollers, secure elements can improve device integrity and lead the way in establishing trust relationships and AES key protection.
NXP Semiconductors' LPC18Sxx and LPC43Sxx microcontrollers are an extension of the existing LPC1800 and LPC4300 series. Both microcontrollers add hardware features for code and data protection (Figure 3). The LPC18Sxx and LPC43Sxx series are equipped with a variety of high-end connectivity features including Ethernet, two Hi-Speed ​​USB and SDIO (the fastest data connection between WiFi modules). In addition, some versions also support graphic LCD connections. Most NXP LPC microcontrollers offer Code Read Protection (CRP), a feature that can be used to protect developer code. Additional security features include an AES-128 hardware accelerator, a true random number generator, and two 128-bit OTP Keys in a one-time programmable memory for storing AES keys.
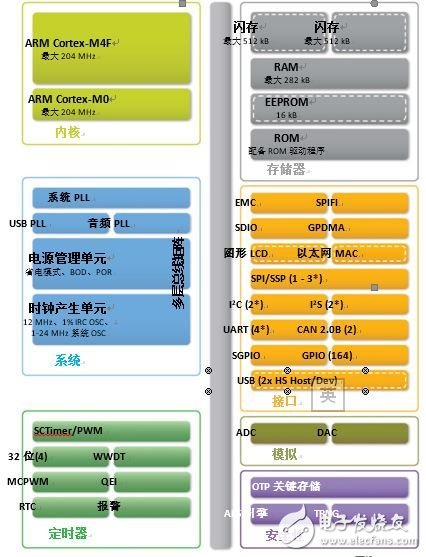
Figure 3: LPC43Sxx Functional Block Diagram The LPC18Sxx provides similar functionality to the Cortex-M3 core.
Two 128-bit One Time Programmable (OTP) key locations help prevent keys from being remotely extracted after a software attack. Once the key (in encrypted format) is written to the OTP, it can no longer be accessed via software or JTAG boundary scan. These keys are only accessible through the internal AES hardware module.
The LPC18Sxx and LPC43Sxx microcontrollers offer built-in Flash (internal 512kB to 1MB) and no built-in Flash version. No built-in Flash version must be booted from an external memory location (ie external QSPI Flash) at reset and run through large internal RAM. In order to prevent the code from being seen by others during the boot process, an encrypted image can be stored in QSPI at reset. The LPC18Sxx or LPC43Sxx will read the encrypted image, verify it by built-in CMAC message authentication, and store it in use. The AES module in the OTP and the 128-bit key are decrypted and the decrypted code is executed from the internal RAM.
The LPC18Sxx and LPC43Sxx microcontrollers are ideal for any IoT application requiring extensive connectivity and high processor performance, including industrial control, industrial automation or diagnostic applications, smart home products (including thermostats and access control), automotive aftermarket and consumer electronics (such as musical instruments, printers, and other networking accessories). Another typical application is the secure IoT gateway (Figure 4).
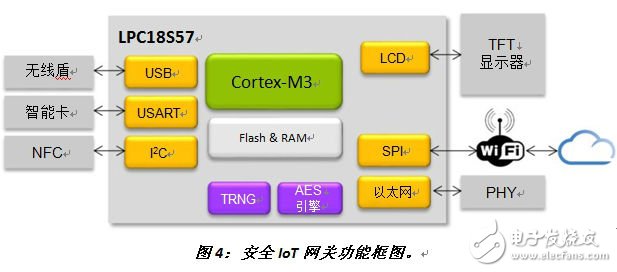
Figure 4: Functional block diagram of a secure IoT gateway.
In this figure, the microcontroller provides a high-speed encrypted connection with hardware-accelerated AES via Ethernet or SPI-based extended WiFi. Cypherbridge Systems is NXP's software partner, offering IoT and Cloud Interconnect software development kits for LPC18Sxx and LPC43Sxx to take advantage of AES hardware acceleration.
Bank-level security can be added simply by connecting the NXP A7 family of security chips to the microcontroller via the I2C interface. The A7 security chip will control hardware accelerated authentication and provide secure storage for permanent certificates required for cloud storage.
ESL Smart SoluTIons has developed EMap, a secure IoT gateway using the LPC18S57 microcontroller and the Cypherbridge Systems software security library (Figure 5).
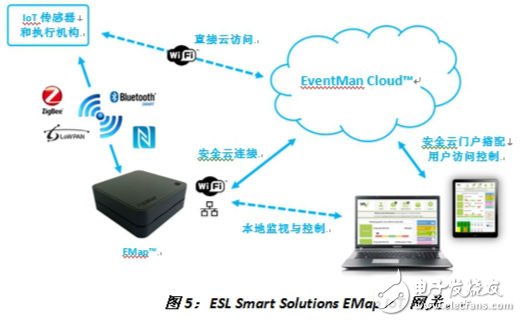
Figure 5: ESL Smart SoluTIons EMap IoT Gateway.
EMap is a highly secure Internet of Things (IoT) gateway that can be delivered as part of an off-the-shelf product or cloud development kit (CDK).
The growing trend of connected devices is unstoppable, with multiple levels of risk. NXP offers embedded designers a variety of solutions to provide the right level of code and data security for specific applications.
Linear light, instead of the traditional lamp, energy saving and environmental protection, easy installation, the power requirements are high, 20W / 45W / 65W, built-in, easy installation, low water level, pay attention to avoid damp environment.TUV certification for the European market.
20/45/65W TUV Certified Linear Driver
Track Light Driver,Tri-Proof Lights Driver,Constant Current Driver 40W
ShenZhen Fahold Electronic Limited , https://www.fahold.com